A) Entercept
B) AppShield
C) Snort
D) StormWatch
F) B) and D)
Correct Answer

verified
Correct Answer
verified
True/False
In Windows 2000 Server, is it necessary to install Network Monitor and Network Monitor Driver separately?
B) False
Correct Answer

verified
Correct Answer
verified
Multiple Choice
In Netware 6.x, what directory contains the Audit log and the Console log?
A) SYS:NOVONYX\SUITESPOT\ADMIN-SERV\LOGS\
B) SYS:ETC\
C) SYS:VAR\
D) SYS:NOVONYX\SUITESPOT\LOGS\
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
In Mac OS X, which log contains information about printing activities?
A) /var/log/lookupd.log
B) /var/log/lpr.log
C) /var/log/secure.log
D) /var/log/system.log
F) None of the above
Correct Answer

verified
Correct Answer
verified
True/False
In Window Server 2003, does the print$ share enable you to view the number of clients currently using the server as a print server?
B) False
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which type of intrusion detection system looks for intrusion signatures on ports, through frame and packet headers, and through commands?
A) Network-based
B) Host-based
C) Auditor
D) Inspector
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which active intrusion-detection tool monitors for intruders and can take action on the basis of preestablished security policies?
A) Entercept
B) Symantec Intruder Alert
C) SecureHost
D) Storm Watch
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
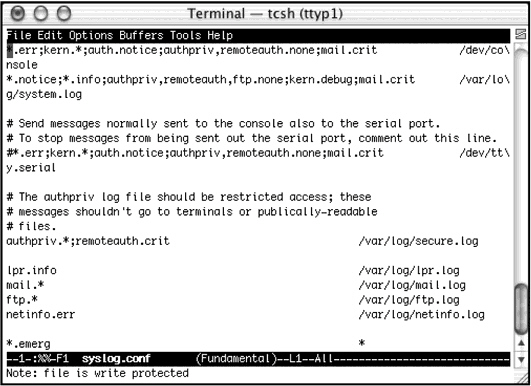 Which file is being edited in the figure above?
Which file is being edited in the figure above?
A) netinfo log
B) lpr.log
C) syslog.conf
D) system.log
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Essay
What five activities are typically encompassed by host-based IDS?
Correct Answer

verified
1. Monitoring logons
2. Monitoring files...View Answer
Show Answer
Correct Answer
verified
2. Monitoring files...
View Answer
Essay
List eight server monitoring functions that can be viewed using the Netware MONITOR command.
Correct Answer

verified
Any eight of the following:
1. General s...View Answer
Show Answer
Correct Answer
verified
1. General s...
View Answer
Short Answer
In Red Hat Linux, the ____________________ Log provides information about jobs that are scheduled to run or that have already run, such as information about the number of minutes until a specific job will run.
Correct Answer

verified
Correct Answer
verified
True/False
If % Network utilization is frequently over 90 percent, that means the network is experiencing collisions and there may be bottlenecks due to the network design, possibly indicating the need to create more or different subnets.
B) False
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which type of IDS looks for excessive use of a computer's resources, such as the CPU or memory?
A) Passive
B) Network-based
C) Inspector
D) Auditor
F) None of the above
Correct Answer

verified
Correct Answer
verified
Essay
What five things do inspectors typically look for?
Correct Answer

verified
1. Files that are changed or newly creat...View Answer
Show Answer
Correct Answer
verified
View Answer
Short Answer
Typically, an IDS ____________________ is software that automatically records information to a log.
Correct Answer

verified
Correct Answer
verified
Short Answer
In Windows Server 2003, the ____________________ log records information about how software applications are performing.
Correct Answer

verified
Correct Answer
verified
True/False
Network Monitor supports event management , which enables a server administrator to set up filters to capture a certain event or type of network activity.
B) False
Correct Answer

verified
Correct Answer
verified
Short Answer
Host wrapper software, which may also be called a(n) ____________________, monitors network activity into or out of the computer, including protocols, packets, broadcasts, remote logon attempts, dial-in attempts, port scanning, and other activities.
Correct Answer

verified
Correct Answer
verified
True/False
Does the Netware Remote Manager allow you to send messages to a particular user or to all users?
B) False
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What are the three principle event logs in Windows 2000 Server and Windows Server 2003?
A) System, Security, Application
B) System, Security, Directory Service
C) System, Directory Service, DNS
D) Security, Directory Service, Application
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Showing 21 - 40 of 86
Related Exams