A) list monitor
B) oneshot
C) btprobe
D) tailingprocessor
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
When monitoring and forwarding events collected from a file containing unstructured textual events, what is the difference in the Splunk2Splunk payload traffic sent between a universal forwarder (UF) and indexer compared to the Splunk2Splunk payload sent between a heavy forwarder (HF) and the indexer layer? (Assume that the file is being monitored locally on the forwarder.)
A) The payload format sent from the UF versus the HF is exactly the same. The payload size is identical because they're both sending 64K chunks.
B) The UF sends a stream of data containing one set of medata fields to represent the entire stream, whereas the HF sends individual events, each with their own metadata fields attached, resulting in a lager payload.
C) The UF will generally send the payload in the same format, but only when the sourcetype is specified in the inputs.conf and EVENT_BREAKER_ENABLE is set to true . The UF will generally send the payload in the same format, but only when the sourcetype is specified in the inputs.conf and EVENT_BREAKER_ENABLE is set to true .
D) The HF sends a stream of 64K TCP chunks with one set of metadata fields attached to represent the entire stream, whereas the UF sends individual events, each with their own metadata fields attached.
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
When setting up a multisite search head and indexer cluster, which nodes are required to declare site membership?
A) Search head cluster members, deployer, indexers, cluster master
B) Search head cluster members, deployment server, deployer, indexers, cluster master
C) All splunk nodes, including forwarders, must declare site membership
D) Search head cluster members, indexers, cluster master
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What happens to the indexer cluster when the indexer Cluster Master (CM) runs out of disk space?
A) A warm standby CM needs to be brought online as soon as possible before an indexer has an outage.
B) The indexer cluster will continue to operate as long as no indexers fail.
C) If the indexer cluster has site failover configured in the CM, the second cluster master will take over.
D) The indexer cluster will continue to operate as long as a replacement CM is deployed within 24 hours.
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Consider the search shown below. 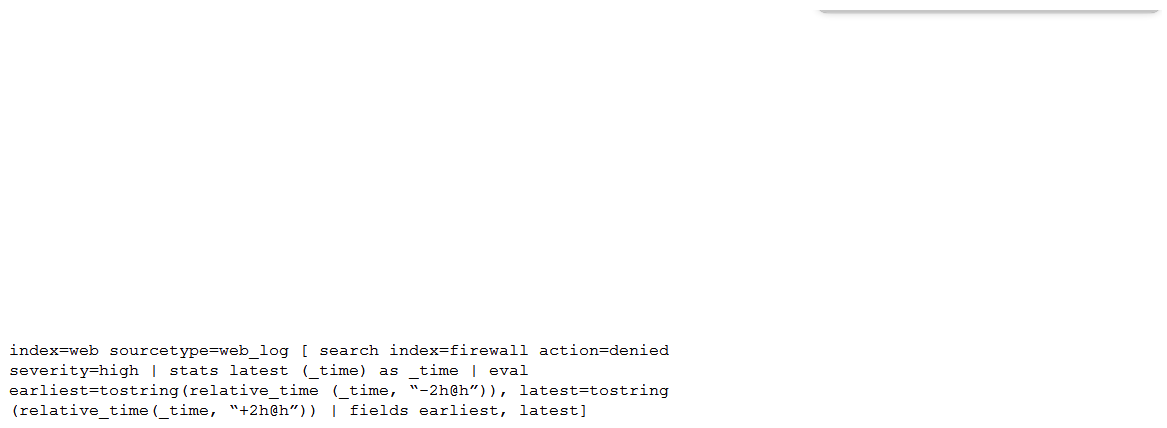 What is this search's intended function?
What is this search's intended function?
A) To return all the web_log events from the web index that occur two hours before and after the most recent high severity, denied event found in the firewall index. To return all the web_log events from the web index that occur two hours before and after the most recent high severity, denied event found in the firewall index.
B) To find all the denied, high severity events in the firewall index, and use those events to further search for lateral movement within the web index. To find all the denied, high severity events in the index, and use those events to further search for lateral movement within the
C) To return all the web_log events from the web index that occur two hours before and after all high severity, denied events found in the firewall index. index that occur two hours before and after all high severity, denied events found in the
D) To search the firewall index for web logs that have been denied and are of high severity. To search the index for web logs that have been denied and are of high severity.
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
The customer wants to migrate their current Splunk Index cluster to new hardware to improve indexing and search performance. What is the correct process and procedure for this task?
A) 1. Install new indexers. 2. Configure indexers into the cluster as peers; ensure they receive the same configuration via the deployment server. 3. Decommission old peers one at a time. 4. Remove old peers from the CM's list. 5. Update forwarders to forward to the new peers.
B) 2. Configure indexers into the cluster as peers; ensure they receive the cluster bundle and the same configuration as original peers.
C) 3. Update forwarders to forward to the new peers. 4. Decommission old peers on at a time. 5. Restart the cluster master (CM) .
D) 4. Decommission old peers one at a time. 5. Remove old peers from the CM's list.
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A [script://] input sends data to a Splunk forwarder using which method?
A) UDP stream
B) TCP stream
C) Temporary file
D) STDOUT/STDERR
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A customer has a number of inefficient regex replacement transforms being applied. When under heavy load the indexers are struggling to maintain the expected indexing rate. In a worst case scenario, which queue(s) would be expected to fill up?
A) Typing, merging, parsing, input
B) Parsing
C) Typing
D) Indexing, typing, merging, parsing, input
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which statement is true about subsearches?
A) Subsearches are faster than other types of searches.
B) Subsearches work best for joining two large result sets.
C) Subsearches run at the same time as their outer search.
D) Subsearches work best for small result sets.
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A customer has been using Splunk for one year, utilizing a single/all-in-one instance. This single Splunk server is now struggling to cope with the daily ingest rate. Also, Splunk has become a vital system in day-to-day operations making high availability a consideration for the Splunk service. The customer is unsure how to design the new environment topology in order to provide this. Which resource would help the customer gather the requirements for their new architecture?
A) Direct the customer to the docs.splunk.com and tell them that all the information to help them select the right design is documented there.
B) Ask the customer to engage with the sales team immediately as they probably need a larger license.
C) Refer the customer to answers.splunk.com as someone else has probably already designed a system that meets their requirements.
D) Refer the customer to the Splunk Validated Architectures document in order to guide them through which approved architectures could meet their requirements.
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Consider the scenario where the /var/log directory contains the files secure, messages, cron, audit . A customer has created the following inputs.conf stanzas in the same Splunk app in order to attempt to monitor the files secure and messages :  Which file(s) will actually be actively monitored?
Which file(s) will actually be actively monitored?
A) /var/log/secure
B) /var/log/messages
C) /var/log/messages , /var/log/cron , /var/log/audit , /var/log/secure , /var/log/cron /var/log/audit
D) /var/log/secure , /var/log/messages
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What is the primary driver behind implementing indexer clustering in a customer's environment?
A) To improve resiliency as the search load increases.
B) To reduce indexing latency.
C) To scale out a Splunk environment to offer higher performance capability.
D) To provide higher availability for buckets of data.
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following server.conf stanzas indicates the Indexer Discovery feature has not been fully configured (restart pending) on the Master Node?
A) ![]()
B) ![]()
C) ![]()
D) ![]()
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A customer has asked for a five-node search head cluster (SHC) , but does not have the storage budget to use a replication factor greater than 2. They would like to understand what might happen in terms of the users' ability to view historic scheduled search results if they log onto a search head which doesn't contain one of the 2 copies of a given search artifact. Which of the following statements best describes what would happen in this scenario?
A) The search head that the user has logged onto will proxy the required artifact over to itself from a search head that currently holds a copy. A copy will also be replicated from that search head permanently, so it is available for future use.
B) Because the dispatch folder containing the search results is not present on the search head, the user will not be able to view the search results.
C) The user will not be able to see the results of the search until one of the search heads is restarted, forcing synchronization of all dispatched artifacts across all search heads.
D) The user will not be able to see the results of the search until the Splunk administrator issues the apply shcluster-bundle command on the search head deployer, forcing synchronization of all dispatched artifacts across all search heads. The user will not be able to see the results of the search until the Splunk administrator issues the apply shcluster-bundle command on the search head deployer, forcing synchronization of all dispatched artifacts across all search heads.
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A Splunk Index cluster is being installed and the indexers need to be configured with a license master. After the customer provides the name of the license master, what is the next step?
A) Enter the license master configuration via Splunk web on each indexer before disabling Splunk web.
B) Update /opt/splunk/etc/master-apps/_cluster/default/server.conf on the cluster master and apply a cluster bundle. Update /opt/splunk/etc/master-apps/_cluster/default/server.conf on the cluster master and apply a cluster bundle.
C) Update the Splunk PS base config license app and copy to each indexer.
D) Update the Splunk PS base config license app and deploy via the cluster master.
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An index receives approximately 50GB of data per day per indexer at an even and consistent rate. The customer would like to keep this data searchable for a minimum of 30 days. In addition, they have hourly scheduled searches that process a week's worth of data and are quite sensitive to search performance. Given ideal conditions (no restarts, nor drops/bursts in data volume) , and following PS best practices, which of the following sets of indexes.conf settings can be leveraged to meet the requirements?
A) frozenTimePeriodInSecs, maxDataSize, maxVolumeDataSizeMB, maxHotBuckets
B) maxDataSize, maxTotalDataSizeMB, maxHotBuckets, maxGlobalDataSizeMB
C) maxDataSize, frozenTimePeriodInSecs, maxVolumeDataSizeMB
D) frozenTimePeriodInSecs, maxWarmDBCount, homePath.maxDataSizeMB, maxHotSpanSecs
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A customer would like to remove the output_file capability from users with the default user role to stop them from filling up the disk on the search head with lookup files. What is the best way to remove this capability from users?
A) Create a new role without the output_file capability that inherits the default user role and assign it to the users. Create a new role without the capability that inherits the default user role and assign it to the users.
B) Create a new role with the output_file capability that inherits the default user role and assign it to the users. Create a new role with the
C) Edit the default user role and remove the output_file capability. Edit the default user role and remove the capability.
D) Clone the default user role, remove the output_file capability, and assign it to the users. Clone the default user role, remove the capability, and assign it to the users.
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following processor occur in the indexing pipeline?
A) tcp out, syslog out
B) Regex replacement, annotator
C) Aggregator
D) UTF-8, linebreaker, header
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
When utilizing a subsearch within a Splunk SPL search query, which of the following statements is accurate?
A) Subsearches have to be initiated with the | subsearch command. Subsearches have to be initiated with the | subsearch command.
B) Subsearches can only be utilized with | inputlookup command. Subsearches can only be utilized with | inputlookup
C) Subsearches have a default result output limit of 10000.
D) There are no specific limitations when using subsearches.
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A customer has a network device that transmits logs directly with UDP or TCP over SSL. Using PS best practices, which ingestion method should be used?
A) Open a TCP port with SSL on a heavy forwarder to parse and transmit the data to the indexing tier.
B) Open a UDP port on a universal forwarder to parse and transmit the data to the indexing tier.
C) Use a syslog server to aggregate the data to files and use a heavy forwarder to read and transmit the data to the indexing tier. Use a syslog server to aggregate the data to files and use a heavy forwarder to read and transmit the data to the indexing tier.
D) Use a syslog server to aggregate the data to files and use a universal forwarder to read and transmit the data to the indexing tier. server to aggregate the data to files and use a universal forwarder to read and transmit the data to the indexing tier.
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Showing 21 - 40 of 62
Related Exams