A) FHRP
B) LACP
C) OSPF
D) STP
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An analyst is developing a proof of concept of a wireless-based attack as part of a penetration test against an organization's network. As part of the attack, the analyst launches a fake access point matching the SSID of the organization's guest access network. When a user connects to the fake access point, the analyst allows the traffic to flow through the access point to the legitimate site while the data traversing the network is logged for latest analysis and exploitation. Which of the following attacks has the analyst successfully performed in this scenario?
A) Bluesnarfing
B) Session hijacking
C) MAC spoofing
D) VLAN hopping
E) Man-in-the-middle
G) A) and E)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A network technician is reading a network diagram and looking for the edge router. Which of the following is MOST likely the symbol used for the router?
A) A circle with four outward arrows
B) A rectangle with two horizontal arrows
C) A square with two circular arrows
D) A triangle with three outward arrows
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following policies prohibits a network administrator from using spare servers in the datacenter to mine bitcoins?
A) NDA
B) BYOD
C) AUP
D) MOU
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A switch is being configured for installation into a new building. The network design is such that the only DHCP server resides in the datacenter. A traditional three-layer network hierarchy is being used, and all buildings have a Layer 3 connection back to the core. Which of the following should the technician configure to get DHCP working properly in the new building?
A) The SMTP relays in the datacenter
B) The MAC address reservations
C) The IP helper address on the switch
D) The ARP forwarding on the switch
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
The server team has just installed an application across three different servers. They are asking that all requests to the application are spread evenly across the three servers. Which of the following should the network team implement to fulfil the request?
A) Proxy server
B) UTM appliance
C) Content filter
D) Load balancer
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A technician needs to connect two routers using copper cables. Which of the following cables would utilize both the TIA/EIA 568a and TIA/EIA 568b standards?
A) Cat5 crossover
B) Cat5e straight-through
C) Cat5e rollover
D) Cat6 console
E) Cat6a straight-through
G) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A network technician does not have access to the GUI of a server and needs to adjust some network properties. Given the command: 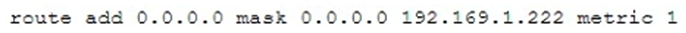 Which of the following is the technician attempting to alter?
Which of the following is the technician attempting to alter?
A) The technician is clearing the route table.
B) The technician is adding a static IP address.
C) The technician is clearing the subnet mask setting.
D) The technician is setting the default gateway.
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A user reports intermittent performance issues on a segment of the network. According to the troubleshooting methodology, which of the following steps should the technician do NEXT after collecting initial information from the customer?
A) Document findings, actions, and outcomes.
B) Establish a theory of probable cause.
C) Establish a plan of action to resolve the problem.
D) Duplicate the problem, if possible.
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A technician is assigned to secure a basic wireless network. Which of the following authentication protocols should the technician use to perform this task? (Choose two.)
A) RDP
B) SNMP
C) WPA2
D) EAP
E) SSL
G) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A network administrator needs to bring a new building online that houses multiple departments. The departments vary in size, with the smallest having 25 hosts and the largest having 140 hosts. When designing the addressing scheme for the new building, which of the following should the network administrator use lo limit the number of wasted IP addresses?
A) Public IPs
B) Private IPs
C) DHCP
D) VLSM
E) Reserved IPs
G) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A network administrator needs to be able to burst datacenter capacity during peak times, but does not want to pay for on-premises hardware that is not used during off-peak times. Which of the following would aid in this scenario?
A) Public cloud
B) SaaS
C) PaaS
D) Hybrid cloud
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A network technician receives a call from a branch office about a problem with its wireless connectivity. The user states the office is hosting a large meeting that includes some online training with local businesses. The guest users have all brought devices to connect to the guest network at the branch office. All users are connected to a single WAP and are reporting that connections keep dropping and network spends are unusable. Which of the following is the MOST likely cause of this issue?
A) DHCP exhaustion
B) Channel overlapping
C) Interference
D) Overcapacity
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A corporation has been the target of hackers who exploited TCP port 80. The network administrator is tasked with securing connections to the web server. Which of the following protocols should be implemented to BEST secure the web server? (Choose two.)
A) HTTPS
B) SSH
C) TLS
D) VNC
E) RDP
F) SFTP
H) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A technician is reviewing network device logs in an attempt to trace an attack that occurred on the network. Which of the following protocols would affect whether or not the technician can properly trace the attack through the network using the logs?
A) HTTP
B) SMTP
C) NTP
D) RDP
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A customer wants to set up a guest wireless network for visitors. The customer prefers to not have a password on the network. Which of the following should a technician set up to force guests to provide information before using the network?
A) Single sign-on
B) RADIUS
C) TACACS+
D) Captive portal
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A company has procured a new office building and started the process of assigning employees to work at that location. The company has also purchased equipment for the new location. There are 5033 laptops, 6000 monitors, and 857 printers. Which of the following steps is the technician most likely to complete FIRST?
A) Create a rack diagram
B) Create a network baseline
C) Create an inventory database
D) Create a port location diagram
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A penetration tester has been tasked with reconnaissance to determine which ports are open on the network. Which of the following tasks should be done FIRST? (Choose two.)
A) Network scan
B) Banner grab
C) Tracert
D) DHCP server check
E) Brute-force attack
G) D) and E)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A technician has deployed an additional DHCP server for redundancy. Clients in certain subnets are not receiving DHCP leases from the new DHCP server. Which of the following is the MOST likely cause?
A) The new DHCP server's IP address was not added to the router's IP helper list.
B) The new DHCP server is not receiving the requests from the clients.
C) The ARP cache of the new DHCP server needs to be updated.
D) The ARP table on the router needs to be cleared.
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A network technician is installing a new PTZ camera for the security department. The camera is capable of being powered via the Ethernet cable, but it is not powering on. The network technician has tested the cable and received positive results. Which of the following is MOST likely the issue?
A) The camera requires PoE+, but the switch is delivering only PoE.
B) A straight-through cable is being used, but the camera requires a crossover cable.
C) The camera is configured for the wrong segmented network.
D) The cable has a bad pinout and needs to be reterminated.
F) All of the above
Correct Answer

verified
Correct Answer
verified
Showing 121 - 140 of 829
Related Exams